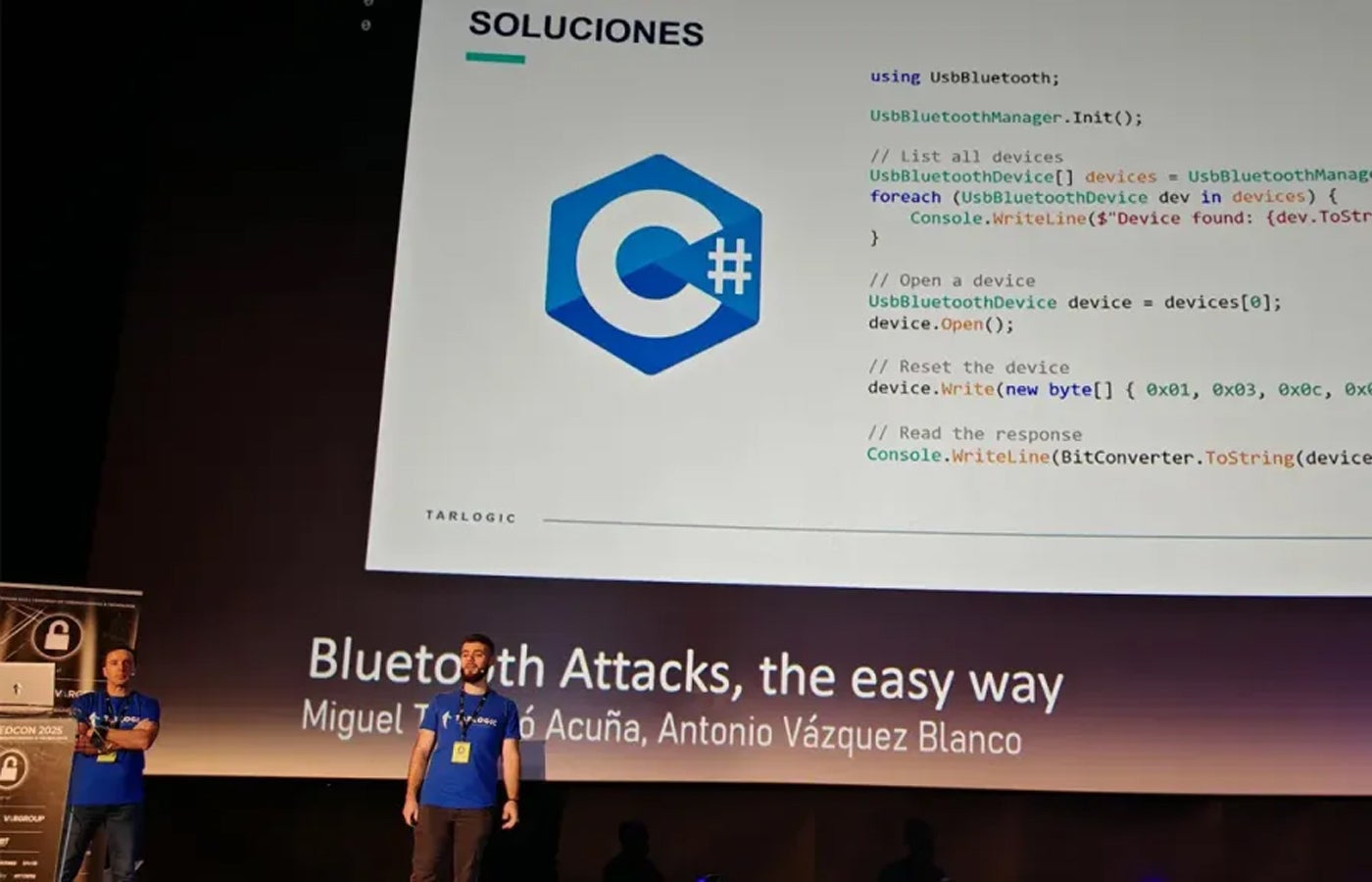
Researchers warn these commands could be exploited to manipulate memory, impersonate devices, and bypass security controls.
Read More
3 days ago
Billions of Devices at Risk of Hacking Due to Hidden Commands